Blog
Agentic Vulnerability Remediation: Fix-in-Place at Scale
Some may say automated. We say agentic, because that's how it's happening. Our CTO on the patcher flow, why fix-in-place at scale is the next step, and why the industry is finally tracking it as emerging technology.

John Amaral
CTO, Co-Founder
Published :
Feb 6, 2026
The Gap Everyone Knows, the Fix Few Have
Our view: Detection scales. Remediation doesn't. Teams find thousands of CVEs; they fix dozens. The backlog isn't a tooling problem; it's a capacity problem. When "fix" can't mean "upgrade" (compliance, pinning, LTS, legacy stacks), the only path is fix in place: backport, patch, and ship artifacts that drop into the stack you're already running.
Doing that at scale used to mean throwing people at it. We don't think that's acceptable anymore, and neither does the market. Agentic vulnerability remediation, thousands of specialized AI agents that research, patch, and validate with humans in the loop, is the direction forward. We've been running it in production for years. Here's how it works in practice, and why we believe it's the next step for every team with serious CVE debt.
Why "Agentic" Instead of "Automated"
Some may say automated. We say agentic, because that's how it's actually happening. It's not a single automation pipeline. It's thousands of specialized AI agents, each with distinct roles, working in swarms with humans in the loop.
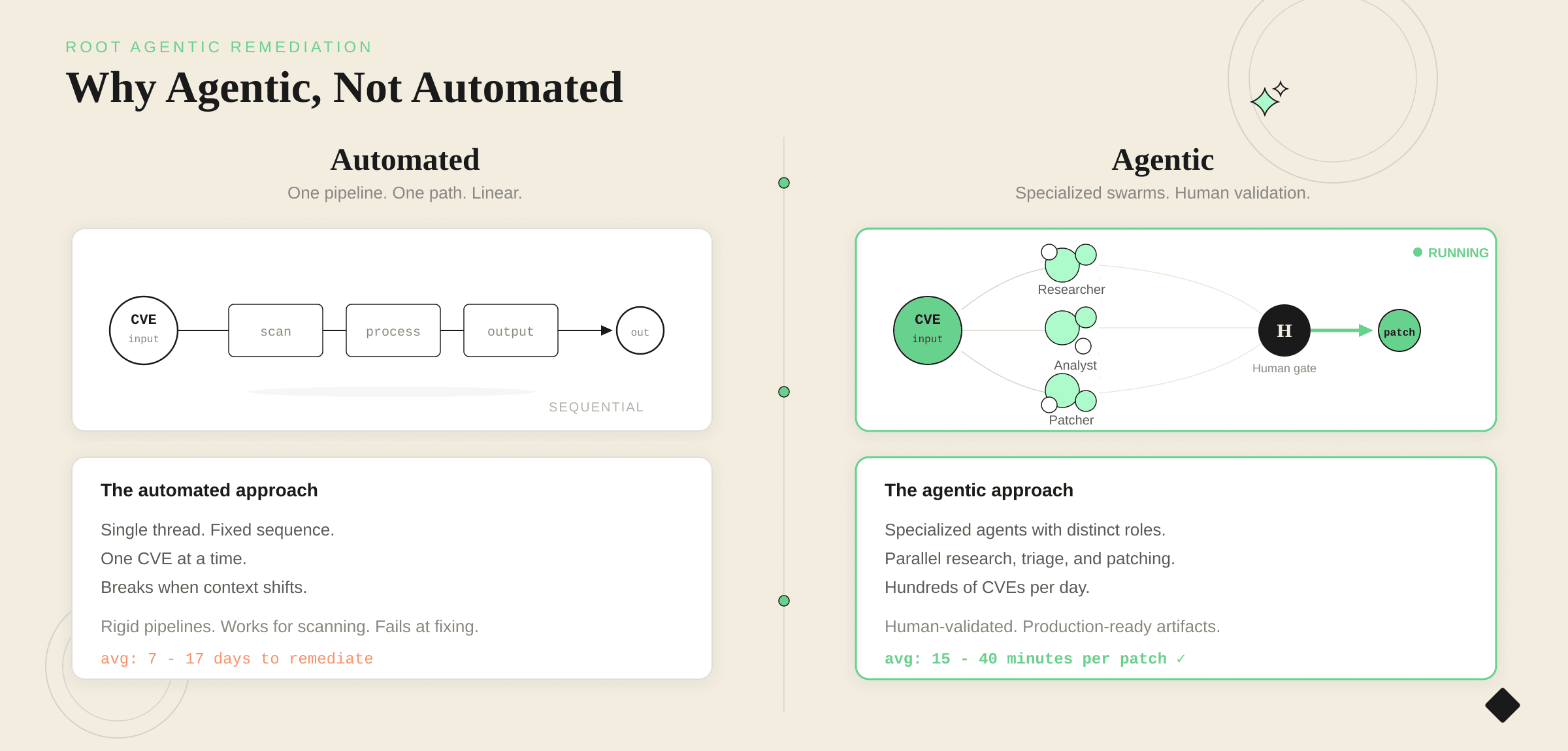
Our Agentic Vulnerability Remediation (AVR) system runs:
Researcher agents that analyze code and repos
Security Analyst agents that triage and prioritize
Workspace Downloader and Complexity Analyzer agents that prepare context
Patcher agents that produce the actual fixes
The heavy lifting is agentic; the sign-off is human. Humans validate, they don't hand-craft. More than four in five patches ship with no code changes from our team, but we don't ship without human review.
Outcomes that matter:
Volume: Hundreds of CVE fixes per day; 20+ new backport patches per day across ecosystems.
Speed: 15–40 minutes per patch, not weeks.
Cost: Typical enterprise cost per CVE fix is over $650. With an automated pipeline built for fix-in-place, it's a fraction of that: the agents do the research and patching; humans do the gatekeeping.
The Patcher Flow: From CVE to Shippable Diff
The heart of AVR is the patcher flow: the sequence from "we have a CVE" to "we have a validated, minimal diff and a report." We built it so builders can see the work, not just trust a green checkmark.
Step 1: Researcher agents
Given a CVE and target package/version, Researcher agents pull upstream sources, analyze the fix in newer versions, and determine whether a backport is feasible and how complex it is. No human has to dig through commits and changelogs first.
Step 2: Security Analyst & workspace prep
Security Analyst agents triage and prioritize. Workspace Downloader and Complexity Analyzer agents prepare the exact codebase and context the Patcher will need (version, dependencies, and scope of the change). Everything the Patcher sees is scoped and consistent.
Step 3: Patcher agents
Patcher agents produce the fix: a minimal diff that addresses the vulnerability in the pinned version you're running, not "upgrade to X." They run in controlled environments with clear boundaries; every change is logged and traceable.
Step 4: Human validation and artifacts
Humans review the diff and the accompanying report.md (and any other artifacts). They approve, request changes, or reject. Only then does the patch become part of our delivered stream: root Patches, RIC, or RLC. So you get automation at scale with a human gate.
Why We Bet on Agentic Remediation
The industry is at a turning point. Shift-left gave us detection at scale; it didn't give us remediation at scale. The next wave has to be remediation that doesn't rely on "upgrade and hope." That means fix-in-place, backporting, and agentic systems that respect human judgment: specialized agents that do the research and patching, humans that validate and sign off.
Root has been running agentic AVR in production for years, delivering patches and secured open source to customers who need fix-in-place at scale. If you're evaluating how to get from CVE backlog to zero debt without burning out the team or betting on "upgrade everything," agentic remediation with humans in the loop is the direction.
Why this approach works:
Closes the gap between "we found it" and "we fixed it" without forcing upgrades or rebases
Scales with CVE velocity while maintaining human validation
Respects existing stacks instead of forcing architectural changes
Delivers artifacts (patches, images, packages) not alerts
Industry analysts are starting to recognize this shift. Gartner's Emerging Tech Impact Radar for Software Engineering tracks what they call "automated vulnerability remediation" as a technology that will materially change how engineering and security teams work. We're more specific: it's agentic. The difference matters: this isn't a linear automation pipeline. It's thousands of specialized agents with distinct roles, working in swarms, with humans in the loop. The "emerging" label fits for the industry: many vendors are still stuck in scan-and-alert mode. But for teams already dealing with thousands of CVEs and limited engineering capacity, this isn't emerging. It's essential.
We're happy to show you the patcher flow live (diffs, report.md, and agent steps) so you can see what "agentic" looks like when it's built for the secure stack.
What to Do Next
See the patcher flow live. Book a demo and we'll walk you through Researcher, Security Analyst, Workspace, Patcher, and human validation, plus the diffs and human-in-the-loop gates. The screenshots above are a start; the live pipeline is where it clicks.
Map it to your backlog. If most of your CVE debt is in open source and you can't "just upgrade," automated fix-in-place is the lever.
Explore the platform. Secured base images, patched libraries, and patch streams that work with what you're working with.
—
John Amaral is CTO and co-founder at Root. He's spent his career building and shipping security and infrastructure products at scale, including as CPO for Cisco Cloud Security, and now leads Root's technical vision. He writes and speaks on shift-out vs. shift-left, dependency control, and why remediation has to be designed for the backlog you actually have.
Continue Reading











